
Secure Development Life Cycle: a new security standard for future-proof railway systems
Modern railway solutions are defined by their connectivity. Before that, railway systems were isolated systems, finished and delivered once all functional requirements were met. With a Secure Development Life Cycle (SDLC) security is embedded in every phase of a continuous development process. After delivery, railway systems are continuously updated to meet ever-changing security requirements.
In a nutshell
- Railway systems have become increasingly connected, making them vulnerable to evolving security threats.
- Because of this evolution railway systems require IT-level security methods.
- SDLC is a model by which software solutions are built using security best practices.
- For railway systems Televic GSP has defined an elaborate set of best security practices in each phase of the development.

What is a Secure Development Life Cycle?
SDLC is a model by which software solutions are built using security best practices. Microsoft introduced it in all its processes, and it has been a staple for software security ever since. In each development phase SDLC provides a list of practices to follow to assure that the security standards of the development are high-end, flexible and future-proof.
But why is this the new standard for Televic GSP? In the past decade, railway systems have become increasingly connected. Before that railway systems were isolated systems, finished and delivered as soon as they fulfilled a list of functional requirements.
Connected solutions, however, are exposed to evolving security threats. This requires a new way of working in which railway systems are continuously updated and upgraded to adhere to the highest security standards. Railway systems have become IT systems, so they require an IT approach to security.
"Railway systems have become IT systems, so they require an IT approach to security."
- Mattias Vanhoutte
Cyber Security Specialist at Televic GSP
Stay up-to-date! Subscribe to our news today.
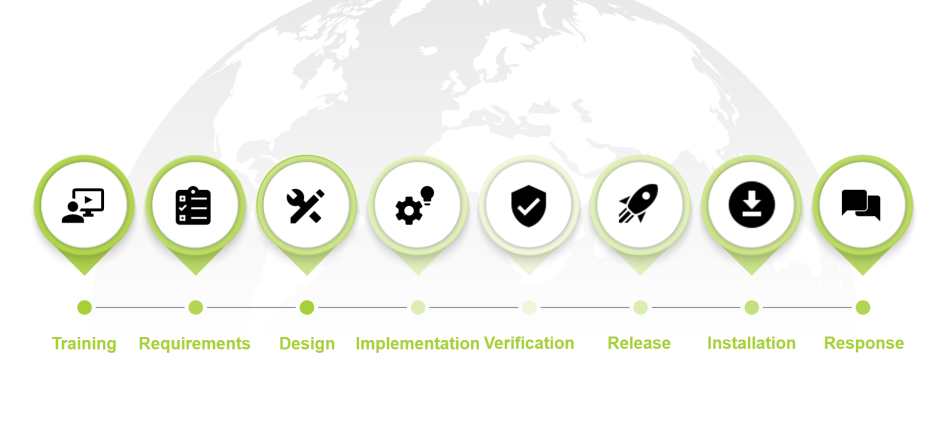
Secure Development Life Cycle defines an elaborate set of best security practices in each phase of the development.
Training
Every team member involved in the development of the product receives rigorous, in-depth training on the security standards and methods, from the software engineer to the project manager.
Requirements
In this stage, cybersecurity and privacy requirements are defined and analysed within the context of the functional requirements. Televic GSP uses its own internal security levels, which are based on industry standards.
Design
In the design phase, a threat and risk assessment analyzes the system for vulnerabilities, examines potential threats associated with those vulnerabilities and evaluates the resulting security risks.
This assessment is executed on different scopes (complete system and/or component level) and allows the development team to consider, document and discuss the security implications of the design. Televic GSPuses parts of the STRIDE model developed by Microsoft to protect against different threats:
- Spoofing
- Tampering
- Repudiation
- Information disclosure
- Denial of service
- Elevation of privilege
Implementation
During the implementation phase the R&D team writes secure code based on secure coding practices and guidelines.
In the development pipeline different security checks are executed on the source code (white box security testing). One example of such a test is vulnerability monitoring of used third-party components. This allows early detection of vulnerabilities in the SDLC.
Verification
In addition to the functional requirements, non-functional security requirements are verified during the testing phase. Examples of these tests are Dynamic Analysis Security Testing (DAST), port scans, web application tests or a black box penetration test executed by an independent third party.
The objective is to uncover potential exposed vulnerabilities resulting from coding errors, system configuration faults or vulnerable (OS) libraries which result in an insecure system.
Release
After the verification phase the software complies with all security requirements and is ready for release. Based on the operational environment settings of the deployments, secure update packages are generated (signed and/or encrypted update packages). This could imply the creation of signed and/or encrypted software update packages to secure the update process on-board the train.
Installation
The process to install secure software updates on-board of a train is only accessible by authenticated and authorized people. Next to the secure update packages Televic GSP provides hardening guidelines to secure the complete deployment (wayside servers & on-board train).
Response
The security of a system evolves over time as new types of security vulnerabilities are uncovered. Systems which are secure today, can be insecure tomorrow. In the response phase – perhaps the most important one – the security of the systems is continuously monitored to keep the systems secure over time. Based on the needs of the customer Televic can provide additional services via a Service Level Agreement (SLA). This SLA could include vulnerability management, incident management and security logging, reassessment of architecture, periodic security tests, notifications, credential management …
This offers customers continuously up-to-date and future-proof security for all railway systems.

Future-proof your railway systems
Developing railway systems through the SDLC model ensures that every Televic GSP system is secure and future-proof to potential security threats, whether it be equipment on-board the train or wayside infrastructure. Even more, a service level agreement guarantees that these systems are always up-to-date and adaptive to future security threats. It transforms our delivery-based service into a partnership with continuous support.
About the author: Mattias Vanhoutte
Mattias Vanhoutte is working as a Cyber Security Specialist at Televic GSP. He brings strong expertise across the whole development cycle, playing a key role in delivering the best security solution taking into account new technologies.



